For this approach i will use my slackpost.sh script to send messages to Slack. More info about it you can find – https://mindau.de/blog/en/en-post-messages-slack-linux/
fail2ban
How to install and configure fail2ban you can find for example here – https://www.digitalocean.com/community/tutorials/how-to-protect-ssh-with-fail2ban-on-ubuntu-14-04
Now edit fail2ban jail.local file
sudo nano /etc/fail2ban/jail.local
add “slack” hook where you want to use it. For example:
.
.
.
[ssh]
enabled = true
port = ssh,sftp,22
filter = sshd
logpath = /var/log/auth.log
bantime = 900
banaction = iptables-allports
findtime = 900
maxretry = 2
action = iptables[name=SSH, port=12345, protocol=tcp]
slack
.
.
.
Now create new config file for slack action:
sudo nano /etc/fail2ban/action.d/slack.conf
copy/paste it
. . . # Option: actionban # Notes.: command executed when banning an IP. Take care that the # command is executed with Fail2Ban user rights. # Tags: <ip> IP address # <failures> number of failures # <time> unix timestamp of the ban time # Values: CMD # actionban = /path/to/slack-report.sh fail2ban ban <ip> . . .
put slack-report.sh to bin folder & restart fail2ban service
sudo service fail2ban restart
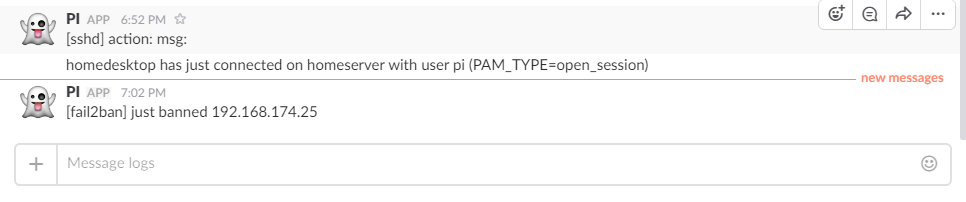
SSH AUTH REPORT
sudo nano /etc/pam.d/sshd
add to file:
session optional pam_exec.so seteuid /path/to/slack-report.sh sshauth
and finaly slack-report.sh
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/sh | |
| # Display usage information | |
| # send notifications from Linux fail2ban, ssh auth and others actions to Slack | |
| function show_usage { | |
| echo "Default Usage: $0 [subject] [action] [msg]" | |
| echo "Example: $0 DATABASE backup succefully" | |
| echo "Custom actions: $0 fail2brain start|stop|ban (ip)|unban (ip)" | |
| echo "Custom actions: $0 sshauth (use variables from pam_exec to generate msg)." | |
| exit | |
| } | |
| # Check for script arguments | |
| if [ $# -lt 1 ] | |
| then | |
| show_usage | |
| fi | |
| # Custom reporting | |
| if [ "$1" = 'fail2ban' ] | |
| then | |
| #slack.conf start and stop not set | |
| if [ "$2" = 'start' ] | |
| then | |
| message='Fail2ban just started.' | |
| echo $message | path/to/slackpost.sh | |
| elif [ "$2" = 'stop' ] | |
| then | |
| message='Fail2ban just stopped.' | |
| echo $message | path/to/slackpost.sh | |
| elif [ "$2" = 'ban' ] | |
| then | |
| message=$([ "$2" != '' ] && echo "[$1] just banned $3" || echo 'Fail2ban just banned an ip.' ) | |
| echo $message | path/to/slackpost.sh | |
| elif [ "$2" = 'unban' ] | |
| then | |
| message=$([ "$2" != '' ] && echo "[$1] just unbanned $3" || echo "Fail2ban just unbanned an ip." ) | |
| echo $message | path/to/slackpost.sh | |
| else | |
| show_usage | |
| fi | |
| # Extra check if not logout (close_session) | |
| elif [ "$1" = "sshauth" ] | |
| then | |
| #slack.conf start and stop not set | |
| if [ "$PAM_TYPE" != "close_session" ] | |
| then | |
| #env is last cmd variables | |
| #subject="SSH Login: $PAM_USER from $PAM_RHOST on $host" | |
| # Message to send, e.g. the current environment variables. | |
| message="$PAM_RHOST has just connected on $HOSTNAME with user $PAM_USER (PAM_TYPE=$PAM_TYPE)" | |
| # message="`env`" | |
| echo $message | path/to/slackpost.sh | |
| fi | |
| # Default | |
| else | |
| echo "[$1] action: $2 msg: $3" | path/to/slackpost.sh | |
| fi |
And results: