After some research and digging, I made my nginx and domain configuration files. If I have something missed, you are welcome to write it in comment here or at Github. Mostly everything are commented so to understand code should be not problem.
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| user www-data; | |
| worker_processes 1; | |
| pid /run/nginx.pid; | |
| events { | |
| worker_connections 1024; | |
| multi_accept on; | |
| } | |
| http { | |
| #don't send the nginx version number in error pages and Server header | |
| server_tokens off; | |
| proxy_hide_header X-Powered-By; | |
| more_set_headers 'Server: Windows 98'; #trololo | |
| # config to don't allow the browser to render the page inside an frame or iframe | |
| # and avoid clickjacking http://en.wikipedia.org/wiki/Clickjacking | |
| # if you need to allow [i]frames, you can use SAMEORIGIN or even set an uri with ALLOW-FROM uri | |
| # https://developer.mozilla.org/en-US/docs/HTTP/X-Frame-Options | |
| add_header X-Frame-Options SAMEORIGIN; | |
| # when serving user-supplied content, include a X-Content-Type-Options: nosniff header along with the Content-Type: header, | |
| # to disable content-type sniffing on some browsers. | |
| # https://www.owasp.org/index.php/List_of_useful_HTTP_headers | |
| # currently suppoorted in IE > 8 http://blogs.msdn.com/b/ie/archive/2008/09/02/ie8-security-part-vi-beta-2-update.aspx | |
| # http://msdn.microsoft.com/en-us/library/ie/gg622941(v=vs.85).aspx | |
| # 'soon' on Firefox https://bugzilla.mozilla.org/show_bug.cgi?id=471020 | |
| add_header X-Content-Type-Options nosniff; | |
| # This header enables the Cross-site scripting (XSS) filter built into most recent web browsers. | |
| # It's usually enabled by default anyway, so the role of this header is to re-enable the filter for | |
| # this particular website if it was disabled by the user. | |
| # https://www.owasp.org/index.php/List_of_useful_HTTP_headers | |
| add_header X-XSS-Protection "1; mode=block"; | |
| # config to enable HSTS(HTTP Strict Transport Security) https://developer.mozilla.org/en-US/docs/Security/HTTP_Strict_Transport_Security | |
| # to avoid ssl stripping https://en.wikipedia.org/wiki/SSL_stripping#SSL_stripping | |
| add_header Strict-Transport-Security "max-age=31536000; includeSubdomains;"; | |
| ### Directive describes the zone, in which the session states are stored i.e. store in slimits. ### | |
| ### 1m can handle 32000 sessions with 32 bytes/session, set to 5m x 32000 session ### | |
| limit_zone slimits $binary_remote_addr 5m; #maybe be depreciated (google it) | |
| ### Control maximum number of simultaneous connections for one session i.e. ### | |
| ### restricts the amount of connections from a single ip address ### | |
| limit_conn slimits 5; #maybe be depreciated (google it) | |
| ##Controlling Buffer Overflow Attacks | |
| client_max_body_size 20M; | |
| client_body_buffer_size 15K; | |
| client_body_timeout 12; | |
| client_header_timeout 12; | |
| keepalive_timeout 15; | |
| send_timeout 10; | |
| ## | |
| # Basic Settings | |
| ## | |
| sendfile on; | |
| tcp_nopush on; | |
| tcp_nodelay on; | |
| types_hash_max_size 2048; | |
| include /etc/nginx/mime.types; | |
| default_type application/octet-stream; | |
| ## | |
| # Logging Settings | |
| ## | |
| access_log /srv/LOGS/nginx-access.log; #@CHANGE TO LOG YOUR LOGFILE | |
| error_log /src/LOGS/nginx-error.log; #@CHANGE TO LOG YOUR LOGFILE | |
| ## | |
| # Gzip Settings | |
| ## | |
| gzip_disable "msie6"; | |
| gzip on; | |
| gzip_comp_level 2; | |
| gzip_min_length 1000; | |
| gzip_buffers 4 32k; | |
| gzip_types text/plain application/x-javascript text/xml text/css application/xml; | |
| gzip_vary on; | |
| # end gzip configuration | |
| ## | |
| # Virtual Host Configs | |
| ## | |
| include /etc/nginx/conf.d/*.conf; | |
| include /etc/nginx/sites-enabled/*; | |
| } |
UPDATE:
If you want more advanced solution, you can try an comprehensive config: Nginx Bad Bot and User-Agent Blocker, Spam Referrer Blocker, Anti DDOS, Bad IP Blocker and WordPress Theme Detector Blocker . With it server config file looks clearer, because #1-#11 and #47-#51 lines (map $http_user_agent $limit_bots…) now is not necessary.
After nginx reload you can test it at: https://asafaweb.com/ . My results for example:
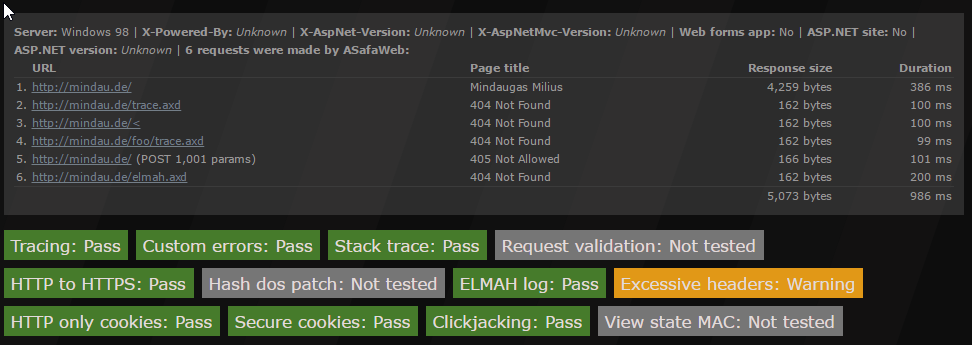
and from https://beyondsecurity.com
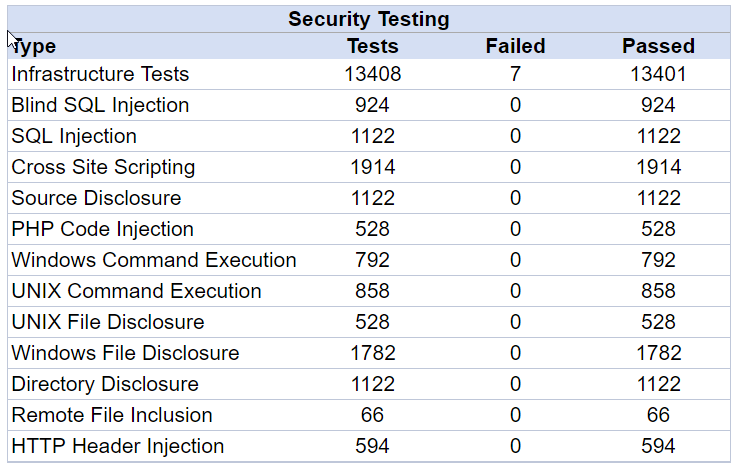
Results a re really impresive, but do not forget. Its only basic prevention from bots and low level hackers. Anyway if you are not building website for governmentit should be okey 🙂
